Are you part of the 79% of internet users worldwide who feel that they have completely lost control over their data? We often feel like this too. The overwhelming traffic, the amount of sensitive activity and information, and the alarming lack of proper regulations all contribute to our general sense of insecurity.
So, is there anything you can do about it? How about using a proxy?
For individual users and organizations alike, proxy servers provide a fair amount of protection. The primary purpose of this technology is anonymity, but the benefits are greater than originally intended. Acting as a privacy shield, proxies enhance our digital security, boost connection speed, and unlock geo-specific content.
Some proxies do these tasks better than others, so you need a foundational understanding of the technology.
Here’s everything that you need to know about how different types of proxies work and why you need one – whether or not you feel threatened by the all-encompassing loss of privacy on the internet.
The basic definition of a proxy server
A proxy is essentially just a server that you use as a middleman between your computer and the internet.
But, let’s start at the beginning, shall we?
Tech experts and enthusiasts generally describe proxy servers as intermediaries, and they are right. However, what most definitions don’t explain exactly what proxies are. Are they, as their name suggests, physical servers? Basic concepts like this one often challenge our digital literacy levels.
What exactly is a server?
A server is either an actual device or a piece of hardware, but it can also be software – a specific program run on a computer. In either case, a server provides a service to other devices and their users, also known as clients. That’s you, me, or anyone else using an internet-enabled computer or phone.
Now, let’s go back to our definition.
Yes, a proxy server is an intermediary or a middleman between your device and the rest of the internet, meaning any website or page you visit, any application you run, or anything you do while online. It can also be described as a gateway, which might be more correct as it implies some kind of a protective layer.
This shouldn’t be hard to visualize. Here’s how it works in practice.
How does a proxy server actually work?
The often-emphasized intermediary role puts a proxy in the middle.
On one side, you have your device, while the rest of the internet is on the other side.
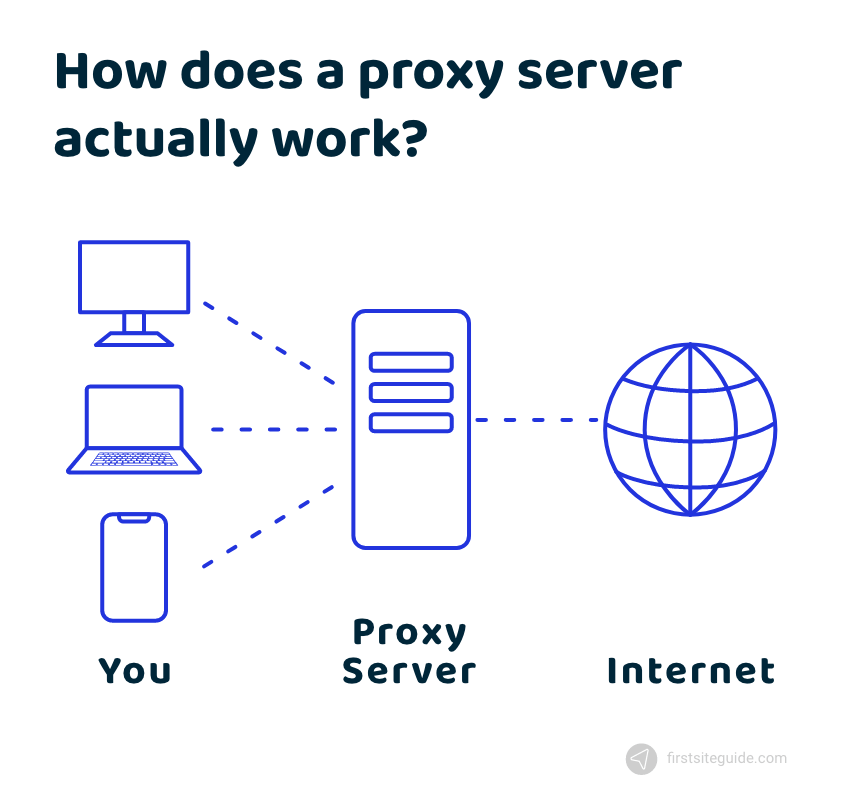
When you’re using a proxy, everything you do on your device that triggers an online action goes through the proxy server before it reaches its final destination on the internet. Say you want to open your Insta page. Before it lands on Instagram.com to get an answer, the request is filtered through the proxy server.
What does the proxy do in the middle of it all?
The technology that proxy servers are based on owes everything to IP addresses.
Every internet-enabled device in the world has a unique IP address, dedicated by a designated internet service provider (ISP). IP is like a physical location, indicating the general area where the device enters the network. Your laptop will have different IPs at home compared to when you’re sun-basking in Hawaii.
Proxies mask your device’s native IP address and replace it with their own. Like every other internet-enabled device, every proxy has an IP address. Your device knows the proxy’s address, so it sends all requests through this gateway.
However, and this is important, the internet sees only the proxy’s IP – and just like that, you are invisible.
The different types of proxy servers
We’ve mentioned earlier that some proxies perform their basic duties better than others. This depends on several factors, but the proxy type is the determining one. Here’s our brief overview of the most popular types of proxy servers.
Forward proxy
When we say “proxy server,” we usually refer to a “forward proxy.” Forward is the most common type of proxy encapsulating everything we’ve just discussed. It plays the middleman position between the client user and the internet by replacing the IP address, which guarantees anonymity and security.
Reverse proxy
A reverse proxy is a forward proxy in the opposite direction. It also reroutes internet traffic, acting as a middleman between an IP address and a target site. The only difference is that it does this in reverse by protecting the anonymity of backend servers and masking the location of the site that you wish to access.
Public proxy
Like public networks, public proxies can be accessed by multiple users simultaneously. Public servers are generally considered less safe and beneficial than private proxies. They are, however, free to use and can come in handy when you need a quick, one-time solution for concealing your IP address.
Residential proxy
Instead of assigning you any random IP, residential proxies replace your location with the location of another user client. The addresses provided by these proxies are super-authentic – they are residential IPs of real devices from anywhere in the world, dedicated to people like you and me by their local ISPs.
Transparent proxy
Transparent proxies are called this because you can see right through them and not notice that they are present. These proxies are primarily used in a corporate environment, where they help employers to monitor and restrict their staff’s online activity. Because there’s no user consent, they are also called “forced.” We should also mention that transparent proxies don’t usually hide your device’s IP address.
Anonymous proxy
Transparent, anonymous, and elite proxies offer various levels of anonymity, from full transparency to complete obscurity. While transparent proxies don’t hide your IP address at all, elite proxies mask both your IP address and the fact that you’re using a proxy, making you appear like any other authentic user. Anonymous proxies are in between: the location can’t see your IP but knows that you’re using a proxy.
Mobile proxy
As the name suggests, a mobile proxy server acts as a middleman between your mobile device and the internet. When using WiFi, your ISP assigns an IP address to your mobile device, revealing its physical location. A mobile proxy hides that, making it look as though you’re using your mobile data network.
Internet service provider (ISP) proxy
An ISP proxy is a residential proxy hosted at a data center. While residential IP addresses provide elite anonymity, data center servers ensure speed and reliability. It’s the best qualities of both proxy worlds that create this powerful combination, ideal for data mining and other complex, long-lasting projects.
Data center proxy
Data center proxies are completely autonomous from any ISP. They offer IP addresses fabricated by hosting companies and cloud service providers to mimic the real thing, and most of them are successful. Some obvious advantages of data center proxies are speed and a greater variety of locations.
The benefits of using a proxy
Proxies sound great in theory, but do you need to use one?
Here’s our resounding yes!
The truth is, access to our browsing histories and personal data have been the end goal of online corporations since the early days of social media and online marketing. Now, everything’s up for grabs. To say that online privacy is in decline is to understate the situation we’re currently in, and it concerns every one of us.
Think about it this way: would you ever share your intimate photos, credit card number, bank statements, medical records, or even your taste in books and music with a complete stranger? Probably not. Oversharing things online willingly is one thing, but keeping records of data about people is another.
Besides, proxies deliver a few other benefits that make browsing a breeze.
Some or total anonymity
Depending on the type, a proxy can offer you some or total anonymity. Either way, it will hide your IP address from the rest of the internet, allowing you to move around freely and share your sensitive information without the usual risk. The pages that you visit won’t be able to keep tabs on your whereabouts.
Speaking of which, do you know what cookies are?
Most websites insert a tracking device into your browser, which allows them to collect a history of your actions on multiple sites. Most tracking cookies are benign. Some help marketing teams tailor retargeting campaigns and personalized ads that follow you around. Others modify prices based on your location.
For legitimate reasons or not, the entire internet wants to get to know you a little bit better. You have two options – quit the internet altogether or stay anonymous. Of course, you don’t have to use a proxy all of the time. However, with everything that we now do online, securing data privacy is becoming a necessity.
Enhanced online security
Anonymity is the precursor to security. Staying hidden from prying eyes has countless security implications, but ultimately it keeps you safe from malicious actors. If there is a hacker on the loose targeting your device, a proxy will ensure that they can’t spot it, infect it, or anything else.
Proxies are very good at filtering malicious websites.
This is especially important in a corporate environment, where different proxies can provide employers better control of their employees’ devices. Some proxies come with built-in scanners that detect and block access to dangerous actors on the internet, such as dummy sites and phishing scams.
Access to locked content
You want to watch The House of the Dragon along with the rest of the world, but you’re stuck in Italy on the premiere evening? So frustrating!
Since HBO Max remains unavailable in many countries worldwide, more and more of us will turn to proxies for help.
Proxy servers can help with this geographic challenge by simply replacing users’ native IP addresses with IPs from locations without any restrictions.
With this same IP address replacement trick, proxies allow you to access all types of restricted content for a variety of purposes. It’s a convenient solution for various private and business applications, from streaming TV shows and playing games to conducting academic research and competitor analysis.
Improved load time speed
While offering all of the benefits that we have shared above, proxies also boost your internet speed.
Some proxies store information on the websites that you visit for later use, which is called caching. Instead of sending requests and processing answers every time you return to the website you frequently use, a proxy server will cache page files and show them on your browser instantly.
This compresses internet traffic and consequently saves bandwidth, resulting in better connection and faster load time. Another bandwidth and time-saver is the proxy’s capability to remove most ads from websites. Ad-blocking is not one of the basic proxy services, but most providers offer it as an extra perk.
The main differences between proxies and VPNs
Proxies are very similar to VPNs, with a few key differences.
If you’re unfamiliar with VPN technology, here’s a quick definition – a virtual private network is an encrypted internet connection through a third-party. If you’re interested in how VPNs work and want to learn more about their benefits, you can find out more about them here.
For the purpose of this article, it’s enough to say that VPNs, like proxies, ensure anonymity and improve security for all users of the world wide web. They also hide your IP address and assign you a new one from different sources, depending on what type of VPN you use. But that’s where their similarities end.
There are two main differences between proxies and VPNs:
- Proxies protect your browser or app, while VPNs protect an entire device.
- Only some proxies have encryption, which is a basic component of VPNs.
Wait. Doesn’t this mean that VPNs are better than proxy services? They do provide better coverage and offer encryption, right? While this is true, it isn’t a ground for comparison. For example, a VPN might feel too clunky if you’re used to multitasking, as you won’t be able to turn it off for location-based apps.
The best proxy servers provide encryption, while some VPNs offer a more flexible approach to using multiple apps at the same time. Both technologies come with sophisticated solutions and cheap variants. Whether you choose a proxy or a VPN ultimately depends on your needs and preferences.
Conclusion
Every single day, a new piece of technology emerges. Most of these tools are designed to make our lives easier in a new way, and there are some inspired security solutions among them as well. Still, nothing beats the necessity and simplicity of a proxy server. Proxies are versatile, easy to use, and very, very reliable.
Before you start using one, remember to choose the right type. Some proxies are better for individual use, and others are more suitable for a business setting. The best providers offer additional features that you might want to consider, but we promise that choosing one is the most complicated part of using a proxy.
The rest of your journey with a proxy is smooth sailing, borderless and private.
The post An Overview of Proxy Servers, How They Work, and Why You Need One appeared first on FirstSiteGuide.
Comments
Post a Comment